
Evil Ant Ransomware Analysis
Evil Ant Ransomware, utilizing the Fernet symmetric cryptography library , encrypts files with . bak extensions and employs code obfuscation to avoid detection. Its payload execution encompasses process concealment and wallpaper alteration, demanding $200 in Bitcoin for decryption. This malware spreads through email phishing, drive-by downloads, and exploiting software vulnerabilities. To combat it, utilize antivirus software, update systems regularly, and enhance cybersecurity awareness . Implement robust data backup strategies, including cloud storage, for effective recovery post-attack. Understanding Evil Ant Ransomware 's tactics is essential for bolstering defenses against such threats.
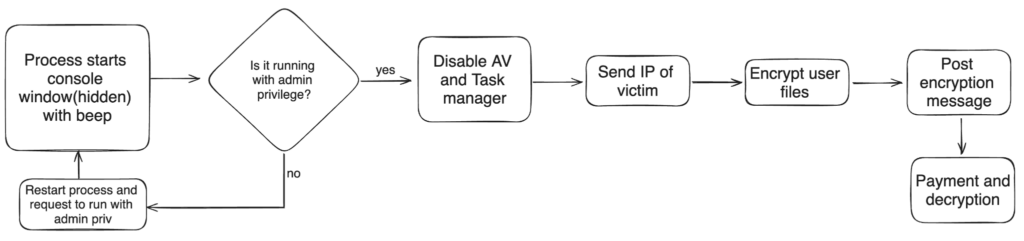
Execution Flow by Netskope
Malware Characteristics
In examining the characteristics of the Evil Ant Ransomware , it is evident that this malicious software exhibits sophisticated encryption techniques and strategic evasion tactics to guarantee successful file encryption and ransom demands.
The ransomware employs advanced encryption techniques, such as the Fernet symmetric cryptography library, to encrypt files with a .bak extension, ensuring the victim's data is securely locked. Additionally, the ransomware utilizes code obfuscation methods to evade detection by security software, making analysis and detection challenging for cybersecurity experts.
The payload execution of Evil Ant Ransomware involves hiding processes, disabling security features like Windows Defender, and changing the victim's wallpaper to display ransom messages effectively. Victim targeting is a critical aspect of this malware, as it aims to encrypt files within personal folders and external drives to maximize impact.
Furthermore, the ransomware demands cryptocurrency payment , typically $200 in Bitcoin, to decrypt the files, emphasizing the anonymity and irreversibility of cryptocurrency transactions in ransom payments.
Infection Methods
Utilizing various deceptive tactics and vectors, malicious actors propagate the Evil Ant Ransomware through a range of infection methods, targeting unsuspecting victims across digital platforms.
Email phishing stands as a prevalent method, where malicious attachments or links are distributed via deceptive emails, tricking users into downloading the ransomware unknowingly.
Drive-by downloads represent another avenue, wherein the ransomware is automatically downloaded when visiting compromised or malicious websites.
Additionally, exploiting software vulnerabilities allows the malware to infiltrate systems without user interaction, emphasizing the importance of promptly updating software to patch potential security holes.
Moreover, social engineering tactics are employed to manipulate individuals into taking actions that facilitate the ransomware's entry, such as clicking on malicious links or downloading infected files.
Removal and Protection
When addressing the removal and protection against the Evil Ant Ransomware , utilizing thorough antivirus software and keeping software updates are essential measures in safeguarding systems against potential threats. Prevention measures such as avoiding suspicious emails, links, and untrustworthy sources can greatly reduce the risk of ransomware attacks. Antivirus software plays an important role in malware detection and removal, providing a layer of defense against malicious threats like Evil Ant Ransomware. Cybersecurity awareness is crucial for recognizing phishing attempts and other tactics used in ransomware attacks.
Regularly updating software and operating systems is important to patching potential vulnerabilities that ransomware exploits. Being cautious of pop-ups and ads on untrustworthy sites can prevent accidental clicks on malicious content . By installing reliable antivirus software and staying informed about cybersecurity threats, individuals and organizations can enhance their defenses against ransomware attacks and other malware intrusions.
Data Backup and Recovery
Effective data backup and recovery strategies are paramount in mitigating the impact of ransomware attacks and ensuring the integrity of critical information assets . Implementing robust backup strategies is essential, including regular backups of important data to prevent loss in the event of a ransomware attack.
Organizations should consider backup frequency based on the criticality of the data , with more frequent backups for sensitive information. Utilizing cloud backups can provide an additional layer of protection by storing data off-site, reducing the risk of data loss due to on-premises compromises.
In the case of a ransomware incident, having reliable recovery options in place is vital for restoring encrypted files without succumbing to attackers' demands. Data protection is enhanced through a combination of backup practices , recovery mechanisms, and proactive measures to safeguard against potential threats, reinforcing the resilience of organizations in the face of malicious attacks.
