
Fileless Malware Explained (Living Off The Land)
In the ever-evolving landscape of cybersecurity, fileless malware has emerged as a significant and stealthy threat. Unlike traditional malware that relies on files stored on the disk, fileless malware operates solely in memory, making it challenging to detect and eradicate.
This article aims to provide a comprehensive understanding of fileless malware, with a particular focus on the Living Off The Land (LOL) project as a notable example. The project utilizes existing operating system files for storage and execution, exploiting legitimate system tools like Powershell and the registry.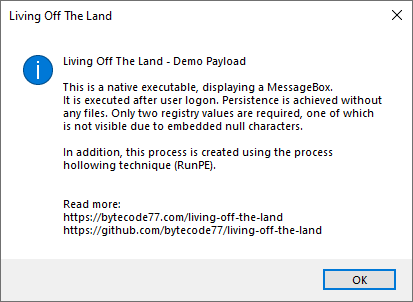
By comprehending the intricacies and stages of execution in fileless malware attacks, organizations can better equip themselves to defend against this evolving threat. This article explores the mechanics of fileless malware and offers insights into detection and prevention techniques to enhance cybersecurity measures.
How Fileless Malware Works
The operation of fileless malware involves the execution and persistence of malicious code without the need for traditional file-based methods. Fileless malware attacks have become increasingly prevalent and pose a significant threat to organizations and individuals alike.
One of the techniques used by fileless malware is memory injection, where the malicious code is injected directly into the memory of a legitimate process. This technique allows the malware to avoid detection by traditional antivirus software that relies on scanning files on disk.
Another commonly used method by fileless malware is PowerShell injection. PowerShell is a scripting language that is built into the Windows operating system and is often used by administrators for system management tasks. Fileless malware takes advantage of PowerShell's powerful capabilities to execute its malicious code without leaving any traces on the file system.
By leveraging PowerShell, attackers can evade detection and carry out their malicious activities.
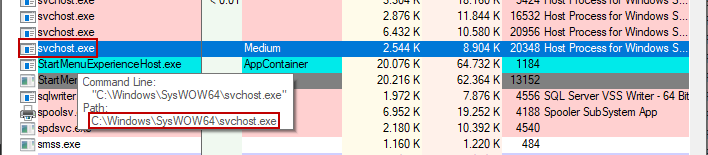
In some cases, fileless malware disguises itself as a legitimate process, such as svchost.exe, which is a system process responsible for hosting services in Windows. By running under the guise of a legitimate process, fileless malware can blend in with normal system activities and avoid raising suspicion.
The use of fileless malware presents unique challenges for defenders, as traditional file-based approaches may not detect or prevent these types of attacks. To effectively defend against fileless malware, organizations need to adopt a multi-layered security approach that includes behavior-based detection, endpoint protection, and network monitoring.
Additionally, regularly updating and patching software, implementing strong access controls, and educating users about the risks of fileless malware are crucial in mitigating the threat.
Techniques to Detect and Prevent Fileless Malware
To effectively detect and prevent fileless malware, it is essential to employ advanced techniques and technologies. Traditional antivirus solutions rely on scanning files for known signatures, which makes them ineffective against fileless malware. However, there are several techniques that can be used to detect and mitigate the risks associated with fileless malware.
One technique is to focus on behavior-based detection. Since fileless malware operates solely in memory, it leaves little to no trace on the disk. By monitoring system activities and looking for suspicious behavior, such as unauthorized access to system resources or unusual network traffic, it is possible to detect fileless malware in action. This approach requires the use of advanced threat detection tools that can analyze and correlate events across multiple endpoints to identify patterns indicative of fileless malware attacks.
Another technique is to leverage machine learning algorithms for fileless malware analysis. Machine learning algorithms can be trained on large datasets of known fileless malware samples to recognize patterns and anomalies in real-time. By continuously monitoring system behavior and comparing it to the learned patterns, machine learning algorithms can identify and flag potential fileless malware attacks. This approach is particularly effective against zero-day attacks, where no known signatures or patterns exist.
Additionally, proactive mitigation measures can be taken to prevent fileless malware attacks. This includes disabling unnecessary system utilities and restricting the use of scripting languages like PowerShell, which are often abused by fileless malware. Regularly patching and updating software can also help prevent fileless malware attacks by addressing known vulnerabilities that attackers often exploit.
