
HTTP/2 Zero-Day Vulnerability Used in Mass DDoS Attacks
The surge in distributed denial-of-service (DDoS) attacks has exposed a new threat known as the HTTP/2 zero-day vulnerability. Exploiting this flaw in the HTTP/2 protocol, threat actors overwhelmed targeted websites with an unprecedented volume of requests, leading to server overload and website takedowns.
This vulnerability is particularly concerning as HTTP/2 is widely used across the web. In response, industry leaders like Amazon Web Services, Cloudflare, and Google are collaborating to mitigate the attacks and safeguard against future exploits.
Discovery of the HTTP/2 Zero-Day Vulnerability
The discovery of the HTTP/2 zero-day vulnerability has raised significant concerns in the cybersecurity community. This HTTP vulnerability, also known as the HTTP/2 zero-day vulnerability, was recently used in a mass DDoS attack that targeted major cloud infrastructure providers such as Amazon Web Services (AWS), Cloudflare, and Google. The attacks, which occurred in late August 2023, utilized a novel technique called HTTP/2 Rapid Reset.
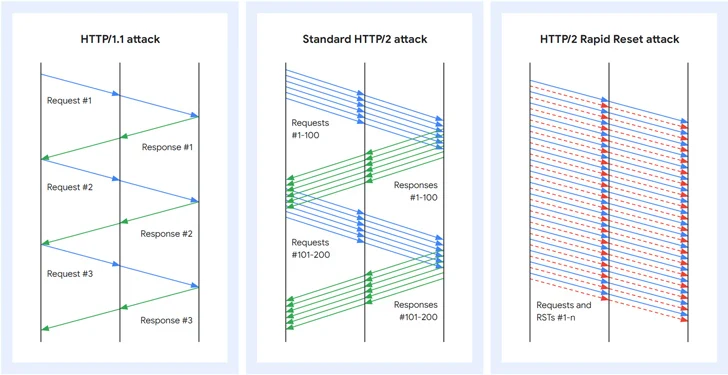
The HTTP/2 Rapid Reset attack takes advantage of a flaw in the HTTP/2 protocol, which allows for multiplexing requests over a single TCP connection. This means that multiple requests can be sent concurrently. However, a client can issue a RST_STREAM frame to cancel a request. The Rapid Reset attack leverages this feature to send and cancel requests in quick succession, overwhelming the server without reaching its configured threshold.

The impact of this vulnerability was substantial, with the attacks peaking at 398 million requests per second for Google's cloud infrastructure, and exceeding 155 million and 201 million requests per second for AWS and Cloudflare, respectively.
This HTTP/2 zero-day vulnerability has provided threat actors with a powerful tool to exploit and attack their victims on an unprecedented scale. It has the potential to take down websites by overwhelming their capability to respond to new incoming requests. Moreover, these attacks can be executed using a modestly-sized botnet.
Given the severity of this vulnerability, cloud infrastructure providers and organizations using HTTP/2 should take proactive measures to ensure protection. Patching systems and limiting the number of concurrent streams can help mitigate the risk of these mass DDoS attacks.
The Impact of the Mass DDoS Attack
The impact of the HTTP/2 zero-day vulnerability and the subsequent mass DDoS attack was significant. It caused widespread disruption and overwhelmed the targeted websites' ability to respond to incoming requests.
The HTTP/2 Rapid Reset attack exploited a zero-day flaw in the HTTP/2 protocol. It unleashed layer 7 DDoS attacks by sending and canceling requests in rapid succession. These attacks specifically targeted Google's cloud infrastructure, AWS, and Cloudflare. Google's infrastructure reached a peak of 398 million requests per second (RPS), while AWS and Cloudflare experienced volumes of 155 million and 201 million RPS, respectively.
The attackers leveraged the ability to reset streams immediately. This allowed them to initiate a barrage of HTTP/2 requests, surpassing the server's concurrent stream maximum and overloading it without reaching its configured threshold. Even with a relatively modest-sized botnet of approximately 20,000 machines, threat actors were able to overwhelm websites and take them offline.
The impact of this attack was unprecedented, providing threat actors with a new tool to exploit vulnerabilities and launch attacks at an unprecedented magnitude. Since HTTP/2 is used by 35.6% of websites, organizations must take proactive measures to protect their systems from similar attacks.
Mitigation Strategies and Future Protection Measures
To address the impact of the HTTP/2 zero-day vulnerability and prevent future attacks, organizations must implement robust mitigation strategies and enhance their protection measures.
The recent mass DDoS attacks that exploited this vulnerability have highlighted the urgent need for proactive actions.
First and foremost, organizations should promptly update their systems and software to patch the vulnerability and ensure they are running the latest versions of the HTTP/2 protocol.
Additionally, organizations should consider implementing rate limiting and traffic filtering techniques to detect and mitigate abnormal traffic patterns associated with DDoS attacks. This can involve setting thresholds for the maximum number of concurrent streams and requests allowed, as well as implementing traffic analysis and anomaly detection tools to identify and block malicious traffic.
Furthermore, organizations should leverage the use of Content Delivery Networks (CDNs) and load balancers to distribute incoming traffic across multiple servers, reducing the impact of DDoS attacks on individual servers.
Regular security audits and penetration testing can also help identify and address potential vulnerabilities.
Conclusion
In conclusion, the HTTP/2 zero-day vulnerability has been a significant concern due to its exploitation in mass DDoS attacks. The severity of these attacks has prompted major players in the technology industry to take measures to mitigate the vulnerability and protect against future exploits.
The discovery of this flaw and the subsequent efforts to address it highlight the ongoing battle to ensure the security and stability of websites using the HTTP/2 protocol.
