
Hackers Use New WhiteSnake Stealer to Automate Account Actions on Victims Accounts
In the ever-evolving landscape of cyber threats, hackers are continuously devising new methods to gain unauthorized access to sensitive information. The latest tool in their arsenal is the WhiteSnake stealer, a sophisticated Advanced Persistent Threat (APT) that is being actively traded on prominent hacking forums.
Unlike traditional APTs, WhiteSnake eliminates the need for a command and control setup and operates solely through a network of servers. With its small file size and robust log encryption, this stealthy tool ensures that its activities remain undetected. Notably, WhiteSnake offers a wide range of features, including the ability to install a remote access beacon, extract data from popular applications and wallets, and even propagate itself within a victim's local network. Moreover, this stealer provides users with the ability to automate account actions, further streamlining their illicit activities.
In this article, we will delve into the capabilities of the WhiteSnake stealer and analyze the potential risks it poses to individuals and organizations.
WhiteSnake Stealer Overview
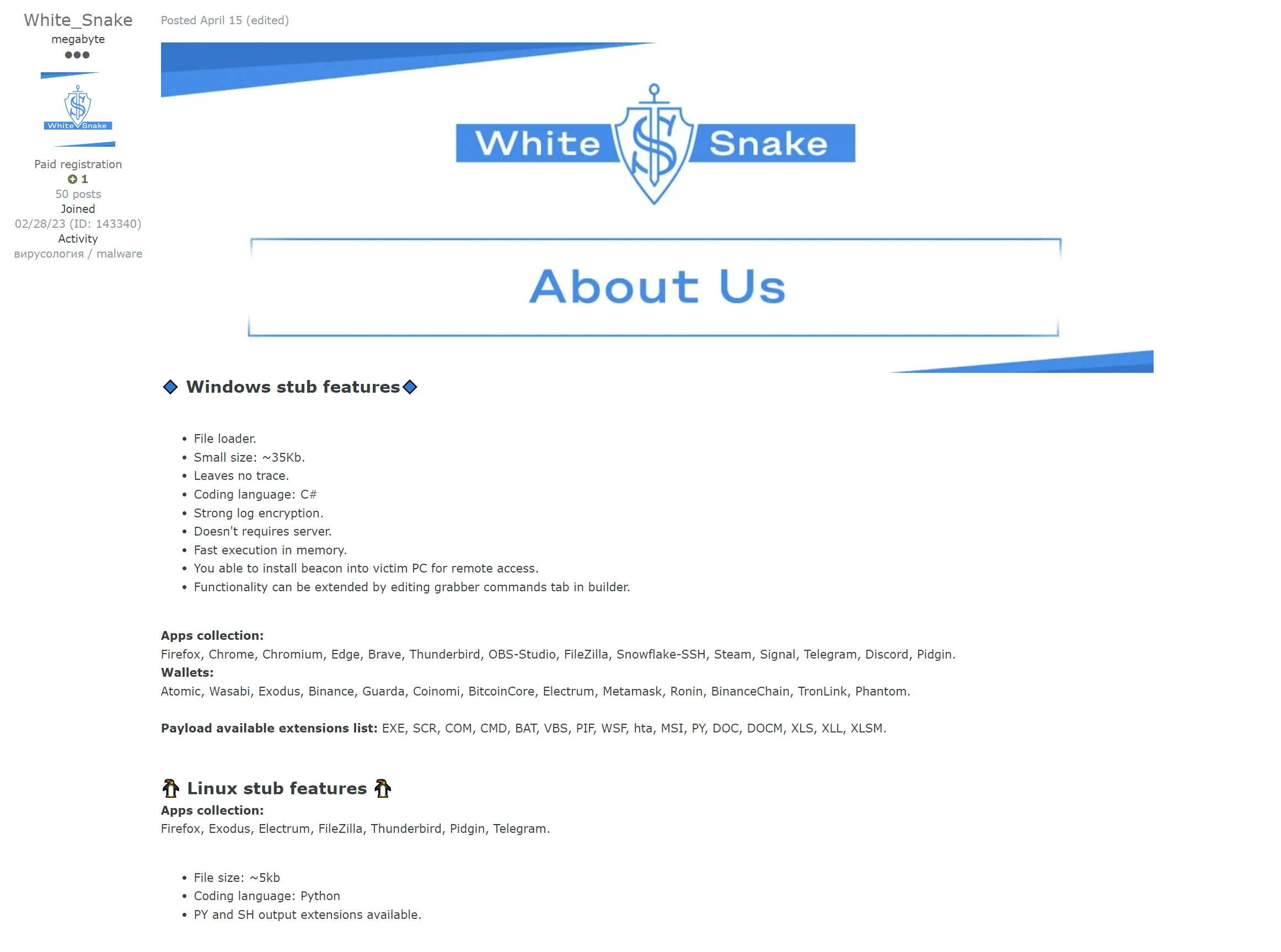
WhiteSnake Stealer is an advanced persistent threat (APT) stealer that has gained popularity among hackers for its ability to automate account actions. This APT stealer has had a significant impact on the cybersecurity landscape, posing a threat to various industries and potential targets. The evolution of APT techniques and tools has allowed WhiteSnake to become more sophisticated and effective in its attacks.
Detection and prevention strategies against WhiteSnake are crucial in mitigating the risks it poses. Cybersecurity professionals must stay vigilant and employ robust security measures to safeguard against this APT stealer. This includes implementing strong access controls, conducting regular security audits, and staying up-to-date with the latest threat intelligence.
The implications of WhiteSnake for privacy and data protection are significant. This APT stealer can compromise sensitive information, including login credentials, financial data, and personal information. The collaboration between law enforcement and cybersecurity agencies is essential in combating this threat effectively. Sharing threat intelligence and coordinating efforts can help identify and apprehend the individuals behind WhiteSnake.
Looking ahead, future trends in APT attacks and countermeasures will continue to evolve. As cybercriminals develop new techniques, cybersecurity professionals must adapt and enhance their defense strategies. This includes implementing advanced detection technologies, conducting regular security training and awareness programs, and adopting a proactive approach to threat hunting. By staying informed and proactive, organizations can better protect themselves against emerging APT threats like WhiteSnake.
Key Features of WhiteSnake Stealer
The key functionalities of the WhiteSnake Stealer include automated account actions and advanced persistent threat capabilities. This stealer is designed to steal credentials and has remote access capabilities, allowing hackers to gain control over victim PCs.
WhiteSnake Stealer supports a wide range of applications and wallets, including popular browsers like Firefox, Chrome, and Edge, as well as cryptocurrency wallets such as Atomic and Electrum. The file size of WhiteSnake Stealer is relatively small, with the Windows stub being around 35Kb and the Linux stub being around 5Kb. It is coded in C# for the Windows version and Python for the Linux version.
WhiteSnake Stealer offers two execution methods: non-resident and resident. The non-resident method steals data and self-destructs, while the resident method steals data and allows for future control of the victim PC.
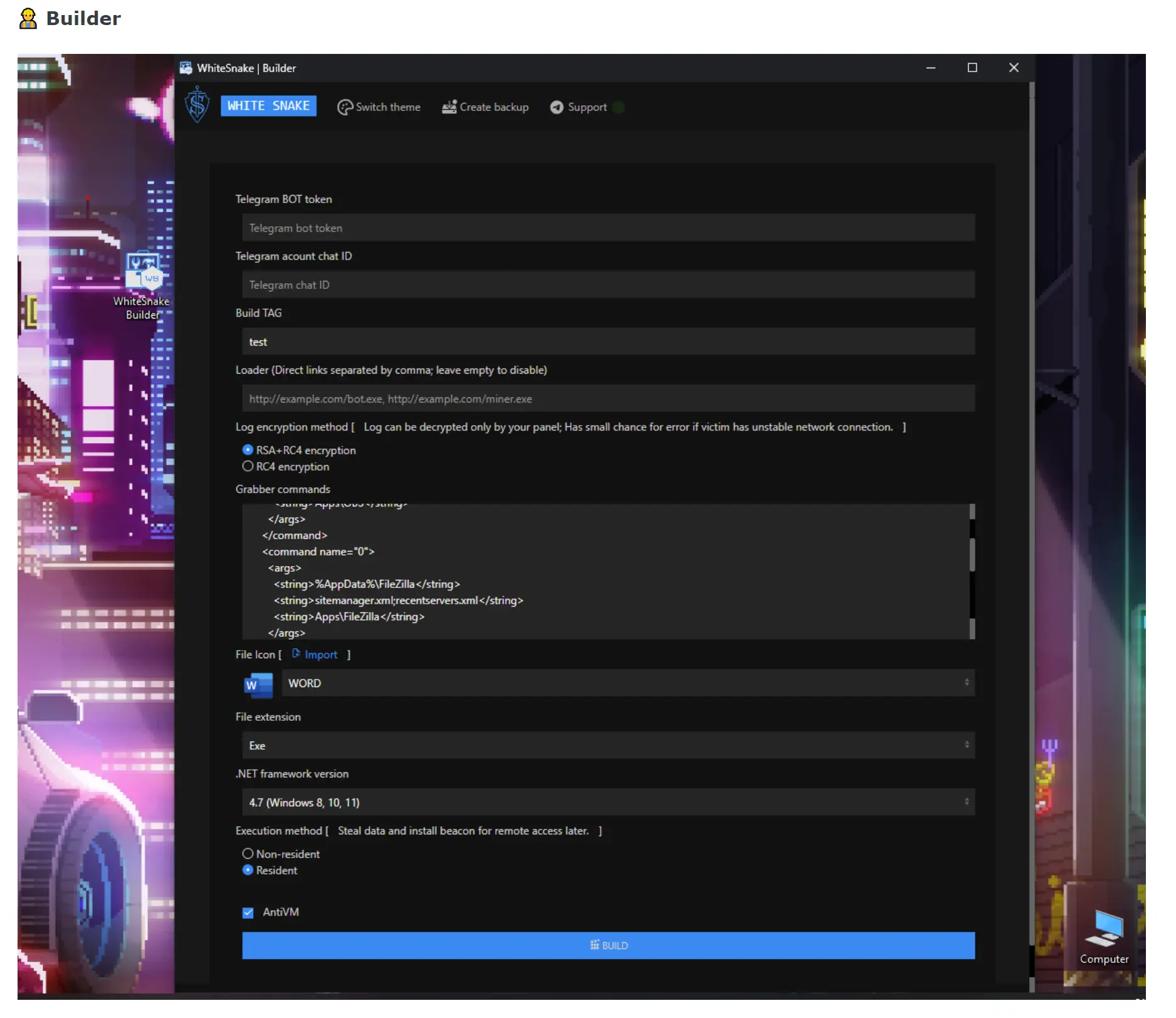
The stealer also includes automatic actions, such as finding proxies, recovering wallet information, and viewing social media profiles, which help save time for the hackers. Additionally, WhiteSnake Stealer offers unique features and regular updates, such as random network traffic generation to confuse researchers and sandboxes, dynamic WinAPI calls, keylogger functionality, and the ability to view running processes and installed applications.
Advanced Automation Capabilities of WhiteSnake Stealer
The advanced automation capabilities of the WhiteSnake Stealer streamline and expedite account actions performed by hackers. This APT stealer has the potential to significantly impact the cybersecurity landscape, as it targets a wide range of potential victims. Compared to other APT stealers, WhiteSnake stands out with its extensive functionality and robust data exfiltration techniques. It can steal data from various applications, including browsers, wallets, and FTP servers. Additionally, it offers features such as keylogging, webcam screenshots, and even spreading itself to other users on the victim's PC.
To protect against WhiteSnake attacks, organizations should implement strong security measures such as multi-factor authentication, regular software updates, and employee training on phishing awareness. Network segmentation and monitoring can also help detect and mitigate potential breaches.
From a legal standpoint, the use of WhiteSnake Stealer is highly illegal and carries severe consequences. Those caught using this tool can face criminal charges, including hacking, identity theft, and fraud.
As for the future, it is likely that WhiteSnake Stealer will continue to evolve and enhance its functionality. Hackers are constantly adapting their techniques, so it is crucial for cybersecurity professionals to stay updated on the latest developments and implement proactive defenses to mitigate the risks posed by this advanced APT stealer.
